Data stealing trojan described as a JPG file (December 31, 2015)

The Dell SonicWall Threats Research team has received reports of a data stealing Trojan described as a JPG file. Upon execution, the trojan steals information from the system and also capable of downloading more malware.
Infection Cycle:
The Trojan has the following description:
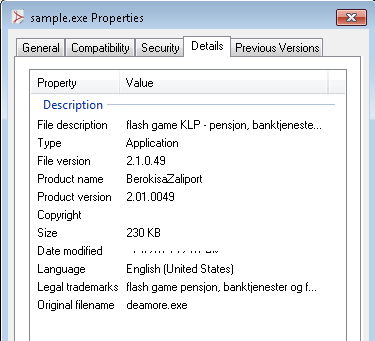
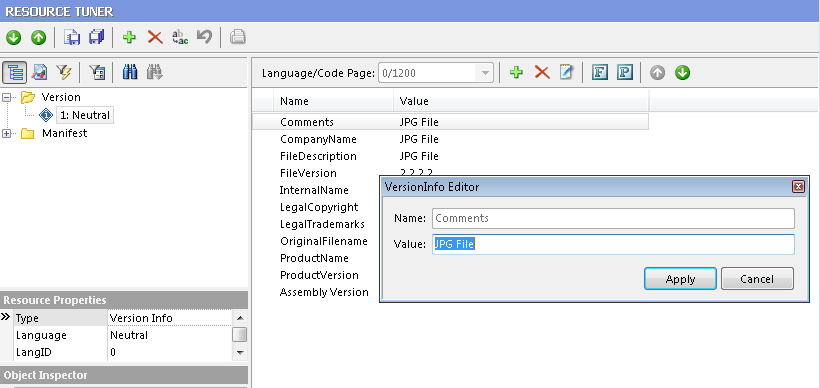
There are few tools available such as Resource Tuner which can be used to change the properties of an executable such as:
- Company Name
- Copyright Notice
- Product Name
- Product Description
- File Version
- Product Version
It copies itself at the following location as explorer.exe to hide itself as a windows process.
It also modifies autorun entries by adding itself at:
It also modifies the firewall policy to add itself to the authorized applications

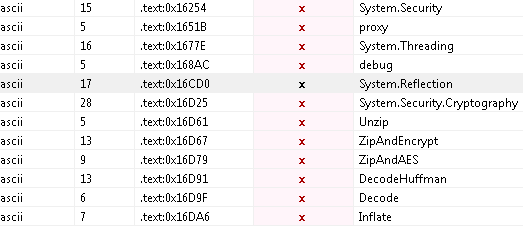
On analysis, the malware contains the following strings which are used to encrypt and decrypt the user information:
The malware contacts the following domain:

Once the CnC server is connected, it steals the following information and sends it to the server at port 5584.
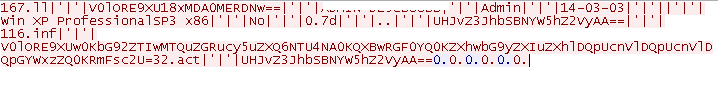
The system information is base64 encoded when sending to the server.
- V0lORE9XU18xMDA0MERDNw== : decodes to WINDOWS_10040DC7
- UHJvZ3JhbSBNYW5hZ2VyAA== : decodes to Program Manager�
- V0lORE9XUw0KbG92ZTIwMTQuZGRucy5uZXQ6NTU4NA0KQXBwRGF0YQ0KZXhwbG9yZXIuZXhlDQpUcnVlDQpUcnVlDQpGYWxzZQ0KRmFsc2U=: decodes to WINDOWS love2014.ddns.net:5584 AppData explorer.exe True True False False
Overall, this Trojan is capable of sending sensitive information out to a remote server.We urge our users to always be vigilant and cautious with any unsolicited attachments specially if you are not certain of the source.
Dell SonicWALL Gateway AntiVirus and Intrusion Prevention provides protection against this threat with the following signatures:
- GAV:Kryptik.EGO_2 (Trojan)
Share This Article

An Article By
An Article By
Security News
Security News