IE 0 day used in watering hole attacks (Jan 2, 2013)

Dell SonicWALL UTM Research team received reports of a new zero day exploit targeting Internet Explorer being employed in watering hole attacks. These attacks target a use-after-free vulnerability in Internet Explorer version 8 running on Windows XP or Windows 7 operating systems. Versions 6 and 7 of Internet Explorer are also vulnerable to this exploit but were not targetted in this attack. This vulnerability is documented under CVE-2012-4792 and Microsoft has released an advisory for it.
A watering hole attack involves planting exploits and payload on compromised sites which are likely to be visited by the victims being targetted. In this case, the site of a think tank headquartered in the US and an organization selling energy generation equipment also headquartered in the US were compromised and the exploits were loaded on to their sites. The attacks were targetting visitors of these sites with a Backdoor Trojan.
Infection Cycle
The exploit is attempted using an SWF and multiple Javascript components. The exploit is only attempted if the flash plugin is installed, IE version is 8, speicifc language packs are installed and Java version 6 is installed. On successful exploit, it leads to the download and execution of a Backdoor Trojan.
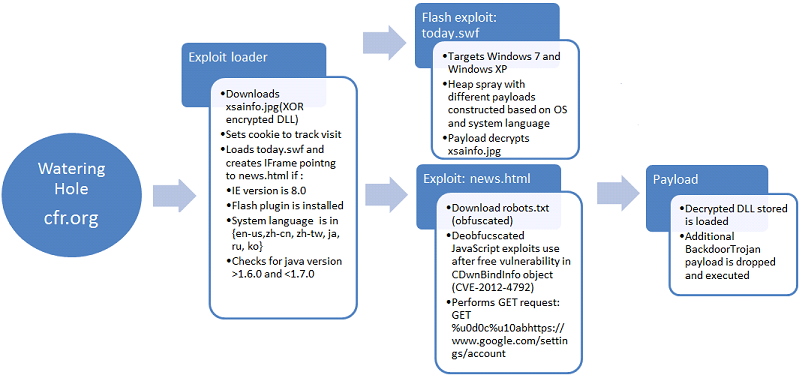
The initial DLL payload is XOR'ed using the key '0x83' and is decrypted by the SWF component. This in turn drops a Backdoor Trojan which does the following:
- It creates a copy of itself appended with random overlay(different hash/footprint in each infection):
%COMMONPROGRAMFILES%DirectDB.exe [Detected as "GAV: Shyape.B (Trojan)" - It creates an instance of iexplorer.exe and injects code in to it
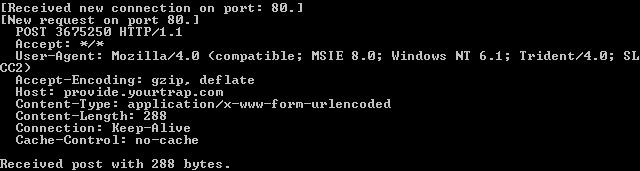
- It attempts to contact a remote server which was found to be offline at the time of analysis. The initial request intercepted with the aid of a simulated server is shown below:
SonicWALL Gateway AntiVirus provides protection against this threat via the following signatures:
- GAV: Bogidow.A (Exploit)
- GAV: Bifrose.N (Trojan)
- GAV: Shyape.A (Trojan)
- GAV: Shyape.B (Trojan)
- IPS: 9445 Windows IE Button Element Use-After-Free 1
- IPS: 9446 Windows IE Button Element Use-After-Free 2
Share This Article

An Article By
An Article By
Security News
Security News