Emissary Keylogger (May 20, 2010)

SonicWALL UTM Research team received reports of a new KeyLogger seen in the wild called Emissary Keylogger. This Keylogger builder has a free version and a paid version being sold in a hacker forum.
The Keylogger builder comprises of two files-- Emissary.exe and Stub.exe. Emissary.exe as shown below is the first released version of the keylogger builder. It requires a malicious user to input email address where the captured keylogs will be sent, the keylogger server name to build, a Fake Message that will popup when the server runs, and system options such as blocking AV sites, adding entry to startup and disabling administrative tasks such as the task manager and Registry editor.
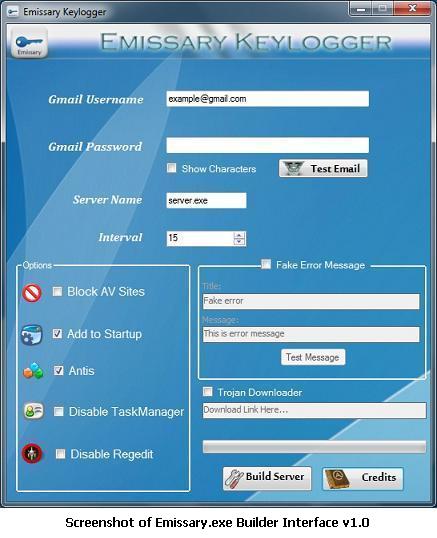
The builder will generate the keylogger server server.exe from Stub.exe, which the malicious user will use to target a victim.
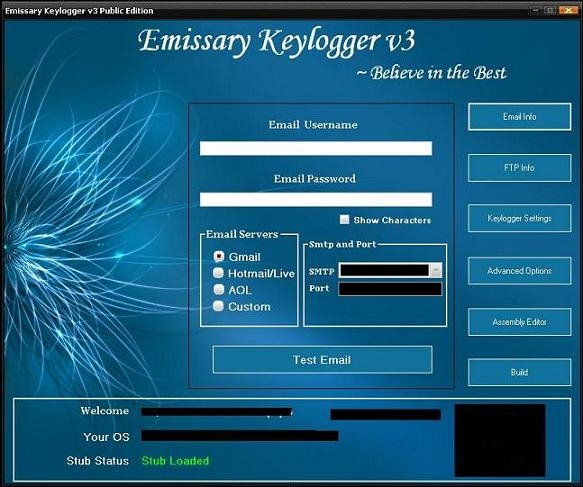
An updated Emissary Builder v3.0 is also available with added features and functionalities such as:
- Supports Gmail, Hotmail and AOL email account
- FTP Backup
- Icon Changer
- Screenshot capture
- Execute Batch file
- Opening Webpage
- Start a Process
- Change Desktop Wallpaper
- Auto Startup Technique
- Adds Startup Registry entry
- Copy itself to Startup folder
- Sends logs in HTML format
- Can Spread via USB
- Download and Execute trojans
- Deletes Cookies
- Logs Clipboard
- Block Websites by modifying LocalHost File
Default entries of this keylogger in Local Hosts file blocks the following security related websites:
- 127.0.0.1 virustotal.com
- 127.0.0.1 www.scanner.novirusthanks.org
- 127.0.0.1 scanner.novirusthanks.org
- 127.0.0.1 www.kaspersky.com
- 127.0.0.1 kaspersky.com
- Sends System Information such as:
- Username
- Machine Name
- Installed logical drives
- IP
- Installed Softwares.
- Disables the following Windows Features by adding registry entries such as:
- Task Manager
- Key: HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionPoliciesSystem
Value: DisableTaskMgr
Data: dword:00000001
- Key: HKEY_CURRENT_USERSoftwarePoliciesMicrosoftWindowsSystem
Value: DisableCMD
Data: dword:00000001
- Key: HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionPoliciesSystem
Value: DisableRegistryTools
Data: dword:00000001
- Key: HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionPoliciesExplorer
Value: NoControlPanel
Data: dword:00000001
- Key: HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionPoliciesExplorer
Value: NoFolderOptions
Data: dword:00000001
- Key: HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionPoliciesExplorer
Value: NoRun
Data: dword:00000001
- Key: HHKLMSystemCurrentControlSetServicesSharedAccessParametersFirewallPolicyStandardProfile
Value: EnableFirewall
Data: dword:00000000
Deletes the following registry entry:
- Key: HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSafeBoot</>
- Key: HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionpoliciessystem
Value: EnableLUA
Data: dword:00000000
- Key: HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionpoliciesExplorer
Value: NoViewContextMenu
Data: dword:00000001
* Startup Folder is usually Documents and SettingsUsernameStart MenuPrograms
* LocalHost is {System Directory}Driversetchosts
Shown below are the screenshots of Emissary Builder v3:
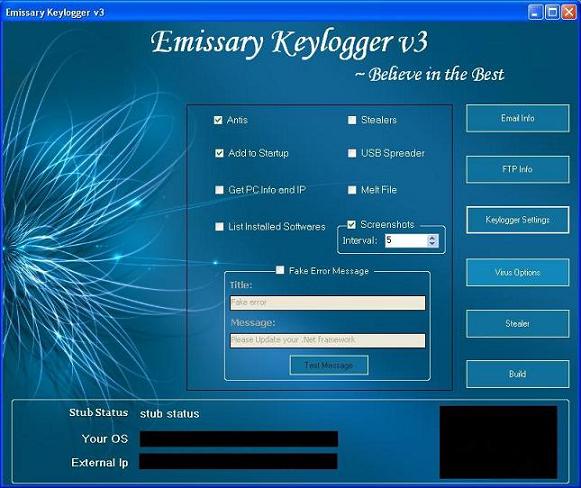
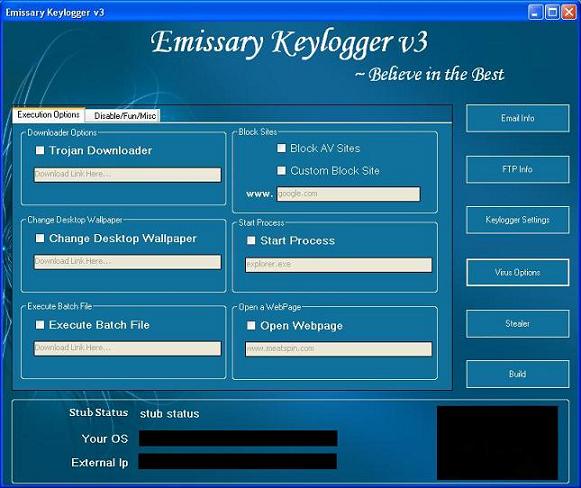
Infection Cycle
Malware authors use different infection vectors to target as many unsuspecting users as possible. They employ social engineering techniques to lure the users into downloading and installing their malware. In one such instance of social engineering tactics used for Emissary keylogger, we saw the malware author use popular video sharing site YouTube which further contained link to a site where the keylogger was being hosted.
1. The Malware author will upload a video on Youtube.com. The Youtube video can pertain to anything that an unsuspecting user might be interested. It will lure the user to click the download link of the video which in fact is a link where the actual keylogger server can be downloaded. In this case, its the www.mediafire.com website.
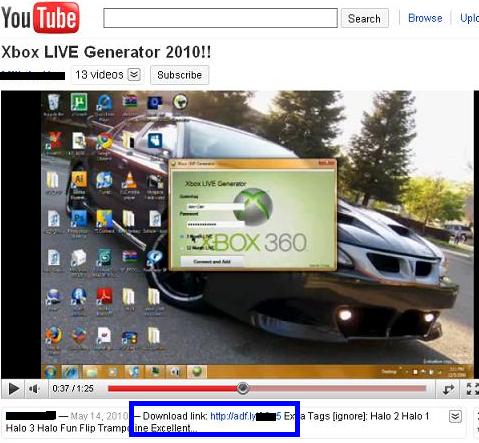
2. With the use of the URL shortening tool, the user have no idea where the download link will be redirected. Once the user clicks the download link, it will be redirected to the website that hosts the keylogger server. The user will then download the file and executes it.
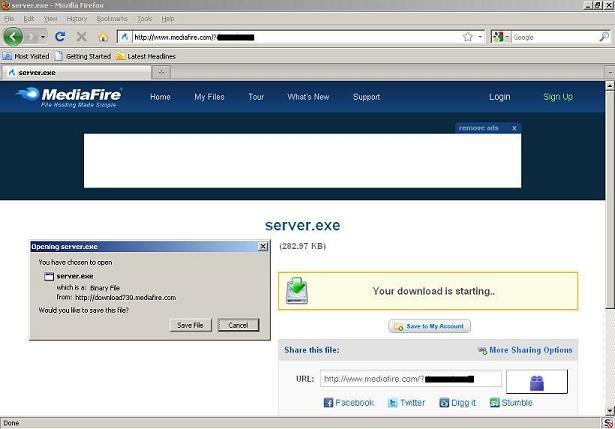
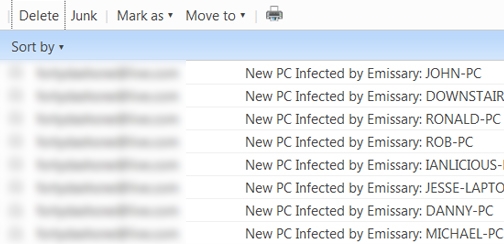
3. The keylogger will then start infecting the system and gathers information and sends it to the author's email. Shown below is an email account of the malware author showing the list of computer machine's infected.
SonicWALL Gateway AntiVirus provides protection against this Keylogger via GAV: EmissaryKeyLogger (Trojan) and GAV: EmissaryKeyLogger_2 (Trojan) signatures.
Share This Article

An Article By
An Article By
Security News
Security News